With a rich history spanning almost twenty years in the field, our array of solutions and services cater to various needs, aiming to strengthen and safeguard your business through flexible security measures.


Our Portfolio




Security Assessment Services
We can exploit vulnerabilities without actually endangering the organization by imitating an actual attacker's actions. This enables the organization to resolve each vulnerability as it arises.
Managed SOC Services
Our fully managed Security Operations Centre (SOC) service frees up our customers' time so they can concentrate on operating their businesses rather than worrying about setting up and managing their own SOC.


Governance, Risk & Compliance
We provide a thorough evaluation of the security posture of your company, pointing out any vulnerabilities and guaranteeing that all of your locations are in compliance with regulations.
Organizations can efficiently respond, investigate, and remediate with the aid of our Digital Forensics & Incident Response services. We are able to locate intrusions, remove intruders, and resume commercial operations.
DFIR Services






Email Phishing Simulation Service
By analyzing how staff members react to phishing emails, our Complete Simulated Email Phishing service helps businesses recognize and reduce phishing risks.
Security Awareness Portfolio
By offering a comprehensive package built on the best security awareness techniques, we provide the ideal answer for enhancing the security culture within your company.


Red Team Services
In order to demonstrate to you how your personnel and security procedures will function to defend your company from a cyber-threat, we will simulate an attack on your network.
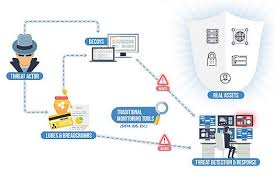
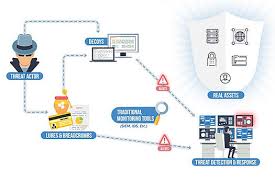
Deception Platform
A single platform with integrated components, CDP can detect and track breaches, deploy and monitor spoofs, and gather all the forensic information pertaining to an advanced threat actor's techniques.


Threat Intelligence Platform
Through the collection and integration of threat feeds from several sources, CTIP empowers security analysts to make intelligence-driven business decisions.
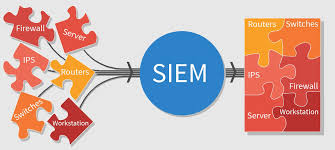
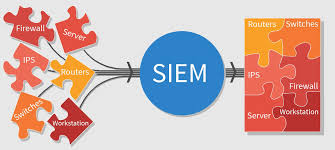
SIEM
With Cydea SIEM, an organization's whole infrastructure can be thoroughly monitored, allowing the security operations team to identify and address risks with greater ease.
Trusted Service
John Doe


Jane Smith
I have been using Cyber Security for years and they never disappoint. Their team is knowledgeable, professional, and always available to help with any security issues. I highly recommend their services to anyone looking for top-notch cyber security solutions.
As a long-time client of Cyber Security, I can confidently say that they are the best in the business. Their expertise and dedication to keeping our data safe have been invaluable to our company. I trust them completely and appreciate the peace of mind they provide.

